Ten steps to successful data governance in mergers and acquisitions
Introduction
The latest EY-Parthenon Deal Barometer reveals an anticipated 12% increase in corporate mergers and acquisitions (M&A) activity for the year 2024, with more than a third of CEOs actively planning to make an acquisition in the next 12 months.
But before the finalization of any merger or acquisition agreement — before the ink even has a chance to dry — companies must address one essential, yet often overlooked, concern: data governance.
Merging complex, disparate data systems and processes is crucial to realizing the benefits of a business combination, but it’s a taxing process fraught with risk. A strategic approach to data governance and migration is necessary to ensure that organizations maintain all the data they need for the future in a usable, searchable form that complies with applicable regulations — without bringing along the costs and risks of outdated, redundant, and otherwise unnecessary information.
‾‾‾‾‾‾‾‾‾‾‾
In this guide, we’ll explore the key steps to successful data governance during and after a merger or acquisition. First, though, let’s consider the risks of failing to include data in M&A planning.
The risks of failing to plan for post-merger data governance
Merging companies is a substantial undertaking. With all of the moving parts to manage, data-related tasks are frequently overshadowed by other essential operational integration activities.
But failing to focus on data governance as entities combine can pose significant risks to the buyer. For example, data fragmentation can plague organizations that merge diverse data sources that generate and store data in different formats. For a media company, failing to understand content rights and licensing agreements for acquired data can disrupt content distribution, leading to ownership disputes and financial losses. For a healthcare organization, merging electronic health record systems and data formats without careful consideration of Protected Health Information (PHI) and regulatory compliance mandates, such as HIPAA, GDPR, or CCPA, can disrupt patient care and result in poor outcomes.
Other risks include the following:
![]() Data loss and inaccuracy
Data loss and inaccuracy
Without a well-defined data migration plan, there is a higher risk that data will be lost or muddled during the transition. Incomplete or incorrect data can lead to poor decision-making and operational disruptions.
![]() Data security vulnerabilities
Data security vulnerabilities
Inadequate planning and poor security measures may expose sensitive data to unauthorized access, including data breaches.
![]() Operational disruptions
Operational disruptions
A poorly planned migration can cause downtime, data access issues, and system errors — all of which can reduce employee productivity and customer service, leading to revenue loss. Incompatibility issues between systems and data structures can also disrupt departmental collaboration and impede the realization of synergies expected from the merger.
![]() Extended timelines
Extended timelines
Without a well-structured plan, data migration may be protracted, raising costs and delaying full operational efficiency.
![]() Compliance violations
Compliance violations
Most global companies are subject to data privacy and data protection statutes, and organizations in heavily related verticals, such as healthcare and finance, must follow stringent regulations; violating any of these rules or regulations due to slow or sloppy data migration can result in legal consequences and financial penalties.
![]() Reputational damage
Reputational damage
Data-related issues, such as security breaches or loss of customer data, can erode customer trust and damage long-term relationships and brand loyalty.
![]() Increased costs
Increased costs
Failing to plan adequately may result in unexpected costs related to fixing data-related issues, implementing security measures, and addressing compliance violations.
![]() Loss of business opportunities
Loss of business opportunities
An inability to harness valuable insights from merged data sets may prevent the organization from making informed decisions, acting quickly on new opportunities, and staying competitive.
By implementing robust data governance practices, the acquiring organization can manage information effectively throughout the merger process and minimize these risks.
A data governance framework for mergers and acquisitions
A data governance framework is a structured approach to managing, organizing, and controlling an organization’s data assets. It is one of the main building blocks in developing a data foundation, providing a set of principles, policies, processes, and responsibilities to ensure that data is properly managed throughout its lifecycle, from creation to disposal. A framework is especially important when organizations are combining their data assets to ensure that nothing falls through the cracks as the merger progresses.
Step 1: Set up a transition team
As soon as the merger or acquisition is announced, reach out to the other organization and begin building a team to manage the data transition. The longer you wait, the greater the chance that someone vital — that is, someone with insights into the newly added data and applications — might leave the acquired entity.
The chief information officer or chief data officer of the acquiring company should lead the team. The rest of the team should consist of representatives from these groups at a minimum:
- Legal: Attorneys who handle M&A should be able to answer questions about potential litigation and any other issues arising from the merger that you need to know about as you ascertain what data and applications to migrate and preserve. Meanwhile, the legal team of the acquired company should advise of any ongoing lawsuits, investigations, court orders, or legal holds that require specific data to be preserved. Legal should also weigh in on their experience with regulatory agencies and relevant lawsuits so you can understand the types of claims that may arise. If the legal department also handles privacy issues, the legal representative should also notify you whether any data is located outside the United States or subject to any data privacy laws. If data privacy is handled by a standalone office or another department, be sure to include a representative from that office or department as well.
- IT: You may need to include representatives from both the buyer’s and the seller’s IT teams. Ask the seller’s IT team to create an asset inventory listing all systems and data in the organization’s custody and control, including cloud-based information and vendor-stored data. You will also need to understand the acquired company’s current data governance program, including how the organization’s data is classified and when its IT team last performed data risk and exposure assessments.
- Finance: The finance team should be involved to make sure that all financial data is accurately transferred.
- Tax: Similarly, tax professionals need to weigh in on the data systems necessary to defend the newly combined company in the event of an audit.
- HR: The seller’s HR team should create checklists for key functions and lines of business. They should also help you track down the devices and data resources of all C-suite leaders who could be named in a related lawsuit — and anyone else whose data may be implicated in the merger — so you can preserve those as part of your records retention program.
As you set up your transition team, establish clear communication protocols to ensure that information flows seamlessly within the team and across departments. You may want to build a central communication hub to collect any inquiries or concerns.
Step 2: Evaluate the acquired organization’s data maturity
To plan for effective integration and identify potential synergies and challenges, you need to realistically evaluate the seller's data maturity. Is the organization reactive (where data is siloed and most requests require ad-hoc processes), integrated (where consistent, repeatable data management processes are in place and building a strong data foundation is a company priority), or optimized (where data currently underpins the business and drives decision-making)?
Taking a proactive approach can help the acquiring organization implement the appropriate risk mitigation strategies and take steps to streamline processes and reduce redundancies. It also gives the buyer insight into the accuracy, consistency, and completeness of the seller’s data, which may need to be remedied before that data is integrated with the buyer’s systems. Finally, an assessment of data maturity offers insights into the acquired organization’s compliance with data-related regulations and legal requirements.
Examine these factors to assess the seller’s data maturity:
- Data foundation: Does the organization have robust and scalable infrastructure to support its data needs? How standardized are the data formats and protocols across the organization? What systems and technologies are in place to ensure data is collected, stored, managed, and used efficiently? How does the foundation support the adoption of advanced data analytics and machine learning technologies?
- Data governance framework: Does the company have well-defined policies, processes, and structures to manage data? Does it have a written records retention protocol? What steps does the company take to monitor and enforce compliance? Who is tasked with oversight? What, if any, technology is used to manage data?
- Data lifecycle: How does the organization manage data throughout its lifecycle, from creation and storage to archiving and disposal? What policies govern data retention and disposal?
- Data quality: How accurate, complete, consistent, and current is the organization’s data?
- Data architecture: How scalable, flexible, and compatible is the existing data infrastructure, including data storage, databases, and integration mechanisms?
- Data security: How does the organization protect its data? What security measures, such as encryption, access controls, and data monitoring, are in place? What vulnerabilities exist?
- Data privacy: What data protection laws apply to the organization? What steps does it take to comply with relevant data protection laws, regulations, and industry standards?
- Data integration: How easily can the organization integrate data from different sources into a single source of truth? Does it use tools such as APIs to facilitate data flow across systems?
- Data analytics and reporting: How does the organization extract insights from its data and make those insights available to executives for use in decision-making?
- Data culture: Are rank-and-file employees aware of the importance of the organization’s data? What training does the organization do to create and maintain a healthy data culture?
Step 3: Create a comprehensive inventory of the acquired organization’s data and tech stack
Next, the team should determine what data, applications, and systems exist in the acquired organization. The goal is to learn what laws apply to the acquired data, whether you need to obtain consent — and from whom — to transfer that data, what steps you should take to access and secure the acquired data, and how you should integrate the new data into your existing IT structure.
If the seller’s IT team has provided you with an inventory of data and technology, use that as a starting point. To identify additional locations where the seller may store data, collect this information:
%204x.png?width=2344&height=2444&name=Group%202486225%20(9)%204x.png)
To follow up on this information, survey leaders from every department, asking questions such as these:
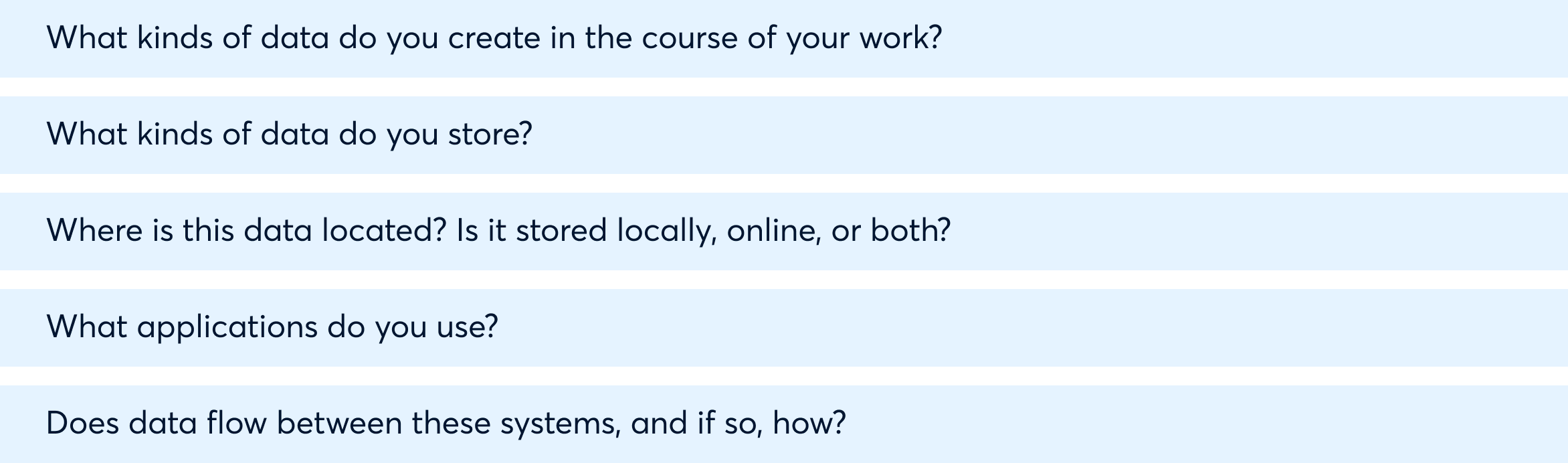
Don’t forget to survey all facilities. Acquired or merged organizations have been known to leave behind computer equipment, file cabinets with hard-copy documents, servers, and server rooms.
As for data hosted by vendors, ask for copies of all service-level agreements, which should explain the vendor’s data security obligations. In addition to standard provisions regarding data security, data protection, and data breaches, ensure that the seller has the right to audit the vendor’s data security and that the seller has transferable ownership and access rights to any data stored in the hosted environment.
Based on what you’ve learned, create a comprehensive data map listing all of the seller’s data sources, including databases, file repositories, document management systems, spreadsheets, and any other places where data is stored. Then take an inventory of each type of data, whether structured or unstructured. For structured data stored in databases, list all database tables, fields, and relationships. For unstructured data stored in file systems, shared drives, and cloud storage, such as documents, presentations, images, and other files, document the location and owner for each type of data.
Step 4: Gather information about acquired litigation matters, investigations, and legal holds
To avoid falling short on your obligations, you must understand what data, systems, and custodians are subject to ongoing legal holds. Ask the seller’s legal team about any pending or anticipated investigations or litigation matters. For each matter, gather and record information about outside counsel, any involved discovery vendors, and custodians, as well as the details of any legal holds, such as specific preservation instructions and the dates those holds were issued. Determine whether the organization uses any software to manage legal holds and information governance more generally.
Obtain a copy of the acquired organization’s records retention schedules and policies. Confirm that the policy addresses all of the data you inventoried in the prior step and that the data classification and level of sensitivity assigned to each type of data make sense. Check for automatic deletion policies, including email management policies, that may be triggered by data migration. From the buyer’s side, determine whether there are any active legal holds that may require the suspension of automatic deletion practices during data migration.
Step 5: Clarify your exposure to data-related laws and regulations
Determine whether the new business increases your potential exposure for violations of data privacy, data protection, and other data-related laws.
For example, if you’ve expanded your geographic footprint, you may also have expanded your need to comply with data privacy laws. If the acquired company collects or stores the personal data of European Union residents, you’ll likely need to comply with the GDPR, which requires you to notify individuals before you process any of their personal data. If you do business with California residents, you’ll need to adhere to similar provisions in the California Consumer Privacy Act (CCPA).
If, through this merger or acquisition, you have added a new line of business in a different industry, it may implicate other rules, such as Payment Card Industry Data Security Standard (PCI-DSS) (credit card information), HIPAA (healthcare data), or FINRA (financial data).
No matter what industry you do business in, make sure you have sufficient measures in place to safeguard any personally identifiable information, protected health information (PHI), and any other sensitive and confidential data. Ignorance of the law is not an excuse, so you’ll need to understand all of the risks in the data you’ve acquired.
This suggestion also extends to proprietary information, including contracts and intellectual property assets. Make sure you have specifically planned how you will identify, collect, and migrate this data. Bear in mind that many organizations lack a clear data taxonomy, leaving contracts scattered across different repositories and file shares.
Here are some of the more problematic data categories that may trigger legal and regulatory obligations:
- Employee data: Personally identifiable information (PII) includes names, addresses, and Social Security numbers as well as payroll information, background check data, employee reviews, and records of any disciplinary actions. This information can trigger laws such as the GDPR, the CCPA, and other laws relating to background checks.
- Customer data: Information about your customers, including their names, email addresses, preferences, purchase history, billing information, and internet browsing habits, may be subject to data protection laws and the seller’s privacy policies.
- Intellectual property: This diverse information, which includes trade secrets, know-how, database contents, and more, requires special protection to safeguard it from unauthorized access or public exposure.
- Operations data: Any data relating to day-to-day business operations, including accounting data, competitor intelligence, market projections, customer and supplier data, and human resources information, needs to be secured.
- Healthcare data: Health plans and healthcare providers and their business associates must protect individually identifiable health information, such as demographic data and details about medical conditions, to comply with HIPAA and the Health Information Technology for Economic and Clinical Health (HITECH) Act. HIPAA’s Privacy Rule and Security Rule establish standards for protecting customers’ and patients’ PHI. Business associate agreements should describe how data should be handled in a merger; generic patient authorizations are insufficient to permit data transfer. In addition, note that the Federal Trade Commission (FTC) regulations, Equal Employment Opportunity Commission (EEOC) regulations, and state laws may apply to biometric data that companies collect from customers, such as fingerprints, retinal scans, and facial imagery.
- Financial data: Data about customer finances, including nonpublic personal information that individuals share with financial institutions along with tax data and cardholder data, is subject to a variety of laws and rules governing its use. For example, the PCI-DSS applies to any business involved in credit card processing, and the Gramm-Leach-Bliley Act (GLBA) limits how organizations can use consumers’ data and requires specific safeguards to protect customer records.
- Telecommunications data: Telecommunications carriers, hardware and software companies, and internet service providers must follow Federal Communications Commission (FCC) guidelines to maintain the privacy of call records and logs, network subscriptions and services, and other subscriber information used for billing.
The key to maintaining legal compliance is identifying what risks exist. The buyer needs to act quickly to determine what data sources will be migrated, then extract the data and analyze it to identify the threats it may pose before classifying it based on its sensitivity and relevance to ongoing business operations. Data categories may include critical, sensitive, confidential, and nonsensitive data. This classification will inform subsequent steps in the inventory process.
Technology, including artificial intelligence (AI), can be used to expedite this process by scanning unstructured data. Advanced data migration platforms centralize your proprietary information so you can collect, search, and manage data at scale. AI and machine learning tools can automatically classify and categorize your information, enabling you to pinpoint sensitive data, reduce unnecessary information, and simplify the organization of what remains.
Step 6: Determine what data, applications, and devices will be migrated
In this step, your goal is to learn whether any valuable data is at risk of loss because it’s not slated for migration. Consider the following data sources:
 Computers
Computers
Find out whether acquired employees are keeping their laptops and bringing their data with them or whether you will issue new computers. If the latter, create a plan to preserve the laptops until you can determine that they do not contain information that you wish to retain. If new laptops are provided, instruct employees on how to migrate any user data that is subject to an active legal hold to the new laptop.
 Devices
Devices
Ask whether the seller has a bring-your-own-device (BYOD) policy. If employees have used their own phones, tablets, and other devices to store company-related information, ensure that those devices will continue to be used; otherwise, you may need to collect their data.
 Email
Email
Determine how you plan to handle email: will you merge employee mailboxes into one system and, if so, what will the retention settings be for the merged system?
 Other applications
Other applications
Inventory and eliminate redundant applications to reduce costs after an acquisition. Specifically, consider whether you will continue the relationship with application cloud providers, move to on-premise instances of the application, or export the application to a new system or application. Important tools to ask about include what software is handling records retention, legal holds, and eDiscovery collection and whether these tools are forensically sound.
 Preserved data
Preserved data
Create a list of data subject to an active legal hold so you can continue to preserve and track it.
 Location
Location
Assess whether any data is created or stored in locations that implicate data privacy or data protection regulations.
 Vendors
Vendors
Find out the status of the company’s relationship with its vendors. Are any vendor fees past due? Is the company overpaying for services? Are the vendors competitors to you or your vendors? Are employees using shadow IT from unauthorized vendors? If any vendors are competitors, have a history of data breaches or other security issues, or are located in a high-risk nation, then move or integrate that data. Also find out what freeware, open-source, or shareware tools are being used.
 Employees
Employees
If employees voluntarily or involuntarily depart the company, you must identify and collect any data that they have in their possession that is subject to preservation obligations. Many employment cases have a six-month statute of limitations, so consider setting that as the date for disposing of employees’ data and devices to avoid the risk of spoliation. It likely makes sense to retain the data and devices of all executives and high-profile employees for longer in case they become targets for litigation.
 Knowledge
Knowledge
Consider how to transfer knowledge that may need to be kept to understand data-related policies and procedures. Find out who the seller’s key points of contact are for records management, litigation, audits, and IT staff responsible for data governance.
Determine whether any of the acquired organization’s data should be deleted rather than combined with your own. Studies have shown that the majority of data stored by enterprises is redundant, outdated, or trivial (ROT) with little or no value. If there is no legal or regulatory reason to retain ROT data, dispose of it to eliminate potential risks.
Step 7: Analyze the scope, ownership, and transferability of the acquired data
When you’ve decided what data you’ll retain, you need to verify that the seller’s ownership rights and access to that data are transferable. Just because the seller has the right to access and use the data now does not mean that it can transfer those rights to a new owner. As a buyer, be sure that you understand any limitations on data transferability, especially in asset sale structures.
These limitations commonly arise from pre-existing contractual restrictions outlined in the seller’s privacy policies or contracts. Scrutinize these policies and consent forms to avoid constraints related to data transferability after the merger or acquisition. Examine any policies provided to customers, suppliers, and the public for language permitting data transfer and usage post-acquisition.
Step 8: Secure representations and warranties from the seller
After creating a data inventory and data map and assessing data ownership, consider what representations and warranties are necessary to allocate risks appropriately. Seek representations from the seller on these matters:
- Data privacy compliance: Identify the privacy laws, regulations, and industry standards that apply to the seller. Have the seller explain how well it is complying with these laws, norms, and policies. The seller should also describe its privacy policies.
- Disclosure of any potential or known data compliance issues: Ask for details regarding any violations of contracts relating to data storage or use, investigations (current or pending) relating to data privacy and data security, and data breaches. The seller should disclose whether any actions, private or governmental, were taken in response to these incidents and how the seller remediated these issues.
- Data security infrastructure: Ask for a copy of the seller’s data security policies and a statement that the seller complies with each policy. Perform additional due diligence if the seller does not have a policy, focusing on the physical, administrative, and technical safeguards the seller uses to protect its data, such as access controls and encryption.
Step 9: Collect and migrate the data
The next determination is how to collect and migrate the data.
As for collection, the first question is whether the data is stored on-premise or in the cloud. If it is in the cloud, find out whether the organization has an API or another mechanism that allows collection. If not, you will need to figure out how to deal with that data.
Collecting and migrating enterprise data generally happens in one of four ways: offsite storage, “big bang” migration, phased migration, and parallel migration.
- Offsite storage. With offsite storage, the acquiring company essentially defers any decisions, instead maintaining all of the seller’s data in storage in case it later finds that that data has value. This approach can have serious downsides. The costs of storing enterprise data are prohibitive, plus keeping all of that data introduces unnecessary risk.
- Big bang migration. Big bang migration happens when all of the seller’s data is moved from its current environment to the new environment in one fell swoop. It’s fast and less complex, so it costs less, but it causes operational downtime that may be expensive. It’s typically best for smaller companies with lower volumes of data.
- Phased migration. In a phased migration approach, the buyer transfers the seller’s data over in small increments, so the old system can remain operational and run parallel with the new system during the migration. This gradual approach can prolong the process, but it eliminates downtime and is less susceptible to errors. This approach works well for organizations that cannot afford system downtime.
- Parallel migration. In a parallel migration, the new system is run alongside the legacy system without transferring historical data until all the bugs are worked out and business processes are running correctly. This approach offers the lowest level of risk, as the business is not disrupted during the migration, and any issues can be addressed entirely before the legacy system is disabled. However, running two systems alongside each other can be expensive, and if it takes an extended period of time to rectify any problems, costs can skyrocket.
Whichever method you choose, you need a well-defined data migration plan. Your plan should include these components:
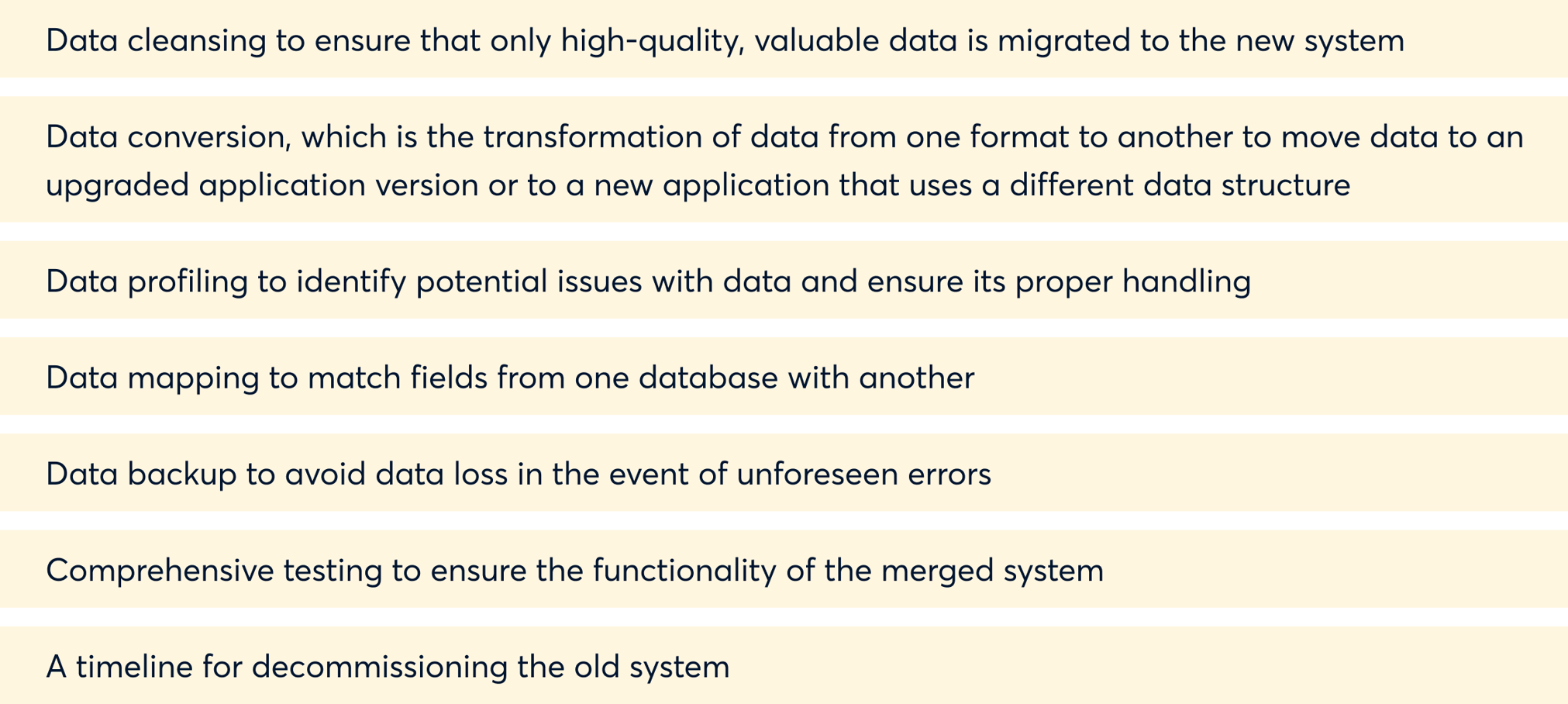
Once you’ve planned for data collection and migration, it’s time to execute your plan — and adapt to any unexpected developments along the way.
Step 10: Implement a robust change management strategy
To facilitate a smooth transition for employees, create a change management program that includes training programs, workshops, and resources to help employees from the acquired company adapt to your data governance processes and systems.
After the merger is complete, conduct a comprehensive review of the entire data management process. Document lessons learned, including successful strategies, challenges faced, and areas for improvement. You can use this information to guide your actions in continuously improving processes and streamlining future mergers.
Build a framework for data governance to set the merged company up for success
Overlooking the nuances of data governance can pose substantial risks to organizations undertaking mergers and acquisitions.
Ultimately, the success of M&As hinges significantly on effective data governance and the establishment (or continuance) of a robust data foundation. As companies merge their data landscapes, the goal should not only be to combine assets but also to enhance the value that these assets bring to the organization. By doing so, companies can leverage data as a powerful tool to drive decision-making, improve operational efficiencies, and create a competitive edge in the market.
The steps outlined above provide a roadmap to navigating the challenges and risks of combining data resources across entities. To ensure your organization is ready to turn its newly combined data stores into a valuable asset following a merger or acquisition, check out our data governance framework checklist below or learn more about how Onna can help eliminate the headaches of governing your data by getting in touch here.
 eDiscovery
eDiscovery Collections
Collections Processing
Processing Early Case Assessment
Early Case Assessment Information Governance
Information Governance Data Migration
Data Migration Data Archiving
Data Archiving Platform Services
Platform Services Connectors
Connectors Platform API
Platform API Pricing Plans
Pricing Plans Professional Services
Professional Services Technical Support
Technical Support Partnerships
Partnerships About us
About us Careers
Careers Newsroom
Newsroom Reveal
Reveal Logikcull by Reveal
Logikcull by Reveal Events
Events Webinars
Webinars OnnAcademy
OnnAcademy Blog
Blog Content Library
Content Library Trust Center
Trust Center Developer Hub
Developer Hub
